Industrial sectors, encompassing everything from manufacturing plants to energy grids, are increasingly vulnerable to cyber-attacks due to the critical nature of their operations. As cyber threats continue to evolve, safeguarding Industrial Control Systems (ICS) and Operational Technology (OT) environments has become imperative. Implementing rigorous cybersecurity standards, such as ISA/IEC 62443-3-3, and deploying industrial firewalls are crucial steps in mitigating these risks.
ISA/IEC 62443-3-3 is part of the ISA/IEC 62443 series, a comprehensive framework designed to secure industrial automation and control systems (IACS). This specific standard focuses on system security requirements and levels, detailing the security capabilities that industrial systems must have to defend against diverse cyber threats.
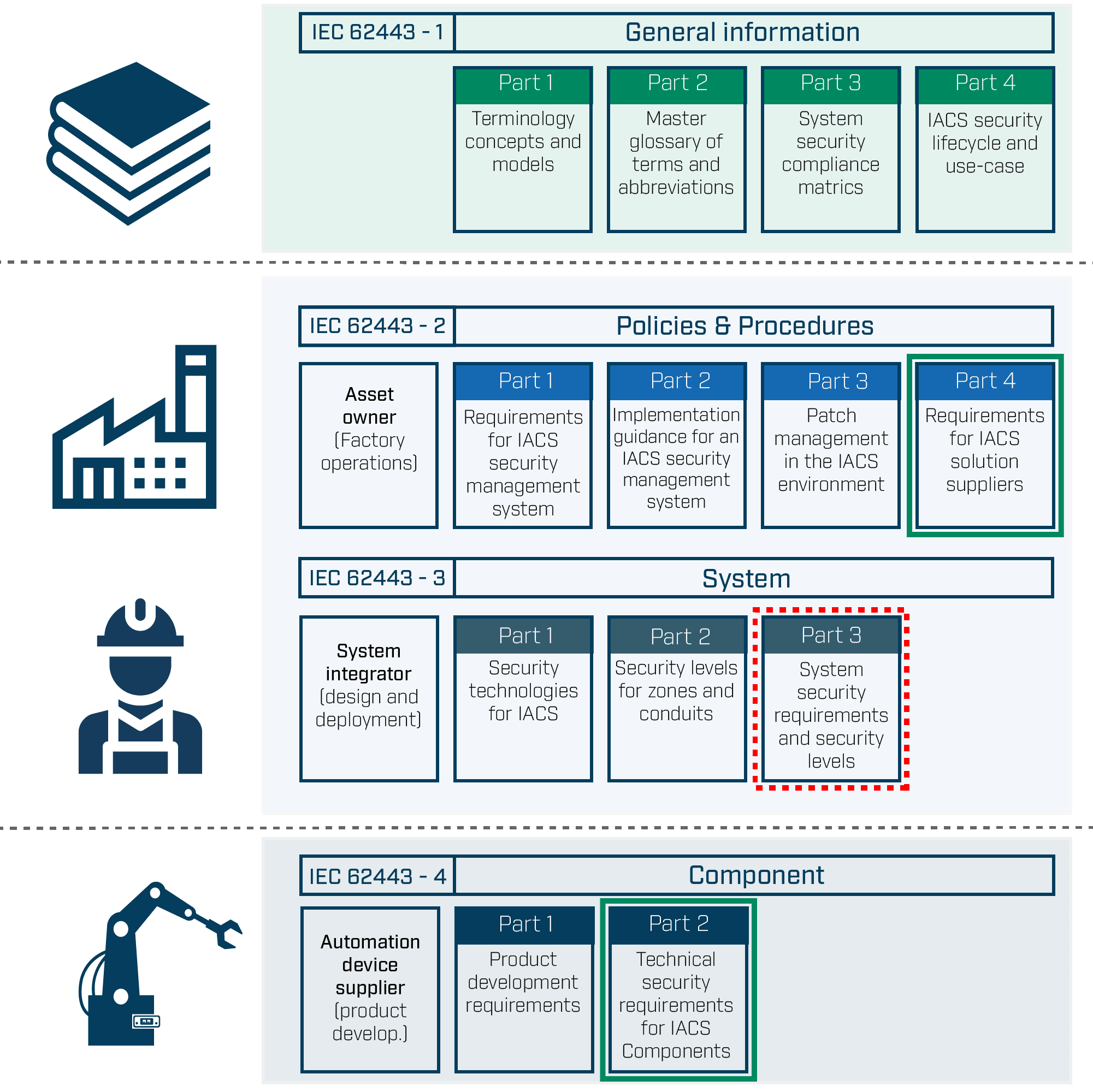
This standard is not only increasingly mandated by regulatory bodies but is also recommended by asset owners, regulators, and insurance companies as a framework for designing and operating secure industrial systems.
Adopting ISA/IEC 62443-3-3 is essential for several reasons:
Asset owners are encouraged to use a risk-based approach to assess cybersecurity needs, understanding how various scenarios impact operations and business. Asset owners are encouraged to use a risk-based approach to assess cybersecurity needs, understanding how various scenarios impact operations and business. To do this, asset owners can use the guidelines in the ISA/IEC 62443 framework, which provide the following four security levels:
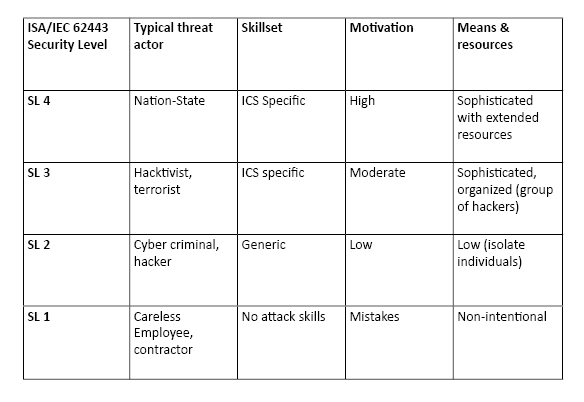
Different systems within the same operational environment may require varying levels of security depending on their potential impact if compromised.
Network segmentation is a pivotal aspect of cybersecurity, highlighted in foundational requirement FR5, "restrict data flow," within the ISA/IEC 62443-3-3 standard. Proper segmentation isolates and protects distinct network areas, mitigating the potential impact of security breaches.
A common approach to segmentation is through Virtual Local Area Networks (VLANs). VLANs create virtual boundaries within a single physical network, enhancing security by separating traffic. While VLANs are suitable for achieving System Security Level (SSL) 1, physical network segmentation is recommended for more stringent security needs, aligning with System Security Level (SSL) 2.
For example, segmentation between a Safety Instrumented System (SIS) and a Distributed Control System (DCS) can be achieved with layer 3 switches and VLANs for SSL 1. However, to meet SSL 2 standards, physical segmentation is necessary, in line with SR 5.1—Network Segmentation: Physical Segmentation.
Higher security levels come with increased costs, so a thorough risk assessment is vital to determine the most cost-effective security measures based on the specific risk profile of the system.
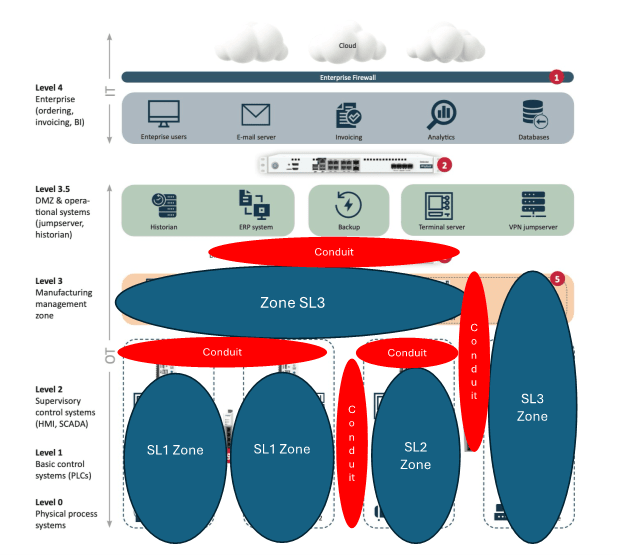
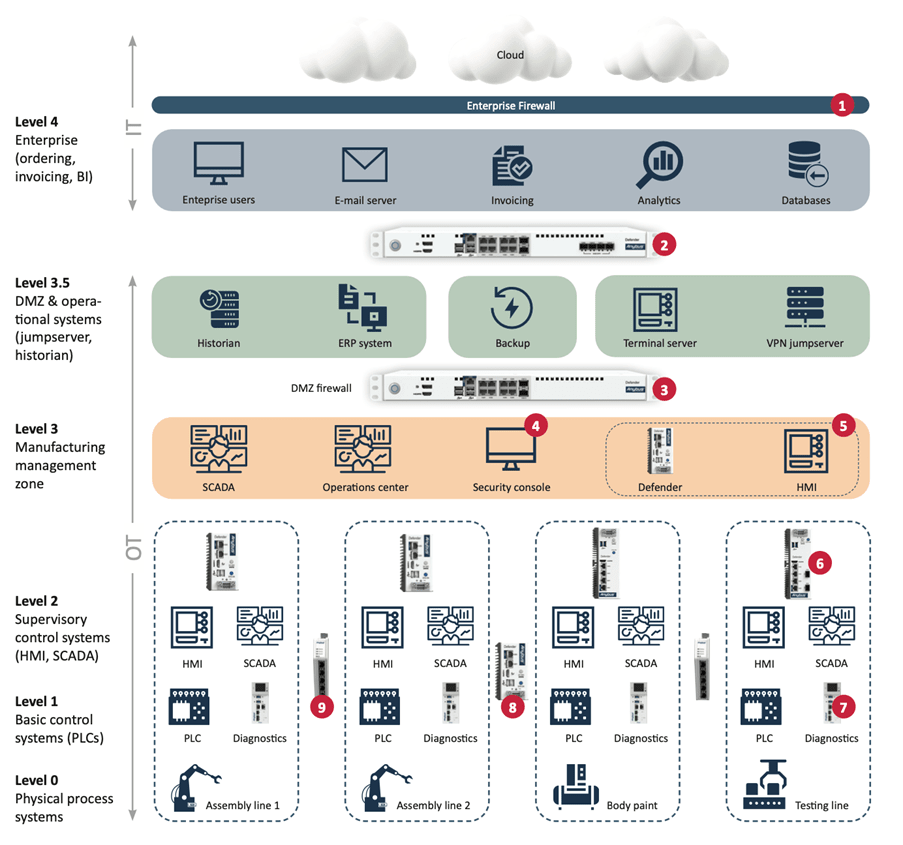
Industrial firewalls play a crucial role in implementing the security measures outlined in ISA/IEC 62443-3-3. Rather than relying solely on a layered defense approach, which can often result in vulnerable architectures, the ISA/IEC 62443-3-3 framework advocates for isolating systems within zones and controlling inter-zone communication strictly.
Industrial firewalls, functioning as conduits, contribute significantly to security by:
Implementing industrial firewalls according to ISA/IEC 62443-3-3 involves conducting regular risk assessments, defining and enforcing security policies, updating and patching security devices, and continuous monitoring and improvement. North/South traffic is controlled by firewalls, while East/West traffic is managed by Coupler Gateways, which only permit industrial protocol content and block unauthorized IP communication between zones.
Adopting ISA/IEC 62443-3-3 and implementing industrial firewalls are not merely best practices but essential measures in today’s cyber threat landscape. By strengthening industrial systems' security through these measures, organizations can protect their operations, ensure regulatory compliance, and maintain their reputation. Embracing these strategies helps create a resilient industrial environment capable of minimizing impact and withstanding sophisticated cyber threats.
Thomas Vasen is Business Development Manager Network Security at Anybus, a division of HMS Networks. With over 25 years of experience in operations and security within telecom, military and critical infrastructures, Thomas now focuses specifically on helping companies managing risks and securing the uptime in their operational technology (OT) environments.


Network security products - Discover the variety of industrial network security appliances that will elevate network protection.