In our previous Cybersecurity article, Thomas Vasen, Anybus Business Development Manager Network Security at HMS Networks, outlined the rise of cyberattacks against industrial automation and explained five strategies companies can adopt to avoid becoming the latest victim. In this article, Thomas discusses the evolving landscape of cybersecurity regulations and standards, their impact on operations and product usage, and how to navigate these changes while maximizing uptime and security.
The cybersecurity landscape is constantly evolving, with emerging standards and regulations driving change across industries. While some regions, such as the European Union (EU), are developing mandatory legislation, others, like the United States, are more focused on promoting adoption through best practices and guidelines. However, all these efforts share a common goal: to establish better-secured operational infrastructures.
Some standards are relevant to Information Security, which concerns Information Technology (IT) operations, while others focus on Operational Technology (OT), aiming to ensure the uptime of machinery and critical infrastructures. It is crucial to adhere to the right standard for your organization or products.
Regulation | Description | Area of focus |
| Purdue Model | Officially called the Purdue Enterprise Reference Architecture (PERA) is a reference model for enterprise architectures, separating Manufacturing Systems from Control Systems from Business Logic Systems. It separates IT from OT, introducing layers creating a defense in depth architecture, making it more difficult for the attacker to reach the critical production systems. | IT/OT organizations |
| NIS2 Directive EU 2022/2555 | EU legislation focused on fortifying cybersecurity in critical sectors, requiring education of executive teams, proactive plans for how to handle attacks, breach reporting requirements among other things. It includes a large liability for non-compliance. | IT/OT organizations |
| EU regulation establishing safety and health standards for machinery, ensuring compliance before introducing machinery to the European market. Updated version classifies for example Autonomous Guided Vehicles (AGVs) as machines for the first time. | OT products | |
| EU Cyber Resilience Act | Approved by EU Parliament in early 2024 and expected to be sealed by the Council later in 2024, this new legislation seeks to impose security requirements on all software and connected devices. It will mandate compliance much like the CE product safety standard before a product can be sold on the European market. The legislation adds security feature requirements on products, hardening them, it puts requirements on the Software Development Lifecycle processes of products and specifically on the vulnerability handling and communications thereof. In addition, it includes the requirement for products to include a Software Bill Of Material (SBOM) providing full transparency of what open source and 3rd party components are used inside the software stack. | IT/OT products |
| RED – Radio Equipment Directive | Radio Equipment Directive is a regulatory framework for placing radio equipment on the market. Sets essential requirements for safety and health, electromagnetic compatibility, and the efficient use of the radio spectrum but also includes cybersecurity requirements. | IT/OT products |
| EN 18031-1, -2, -3 by CEN/CENELEC | This document provides technical specifications of Common security requirements for radio equipment. It is expected to serve as the base for the following EU Cyber Resilience Act. | IT/OT products |
| Widely adopted voluntary set of guidelines enhancing organizational cybersecurity. It provides a structured and flexible approach for organizations to assess and improve their cybersecurity posture and includes 5 capabilities - Identify, Protect, Detect, Respond, Recover. | IT organizations | |
| NIST SP 800-82r3 | Recent addition to the NIST framework specifically focusing on OT Security. It provides guidance on architecture, system hardening, and security countermeasures. | OT organizations & products |
| NERC Critical Infrastructure Protection (NERC CIP) | Requirements securing assets primarily operating in the North American electric system. | OT organizations |
| CIS Controls | A non-profit organization sharing best practice guides with prioritized set of actions to protect organizations and data from cyber-attack vectors. | IT organizations |
| Cyber Trust Mark | FCC initiative based on NIST framework, imposing security requirements on IoT products, currently voluntary with a focus on consumer goods. The intent is to create transparency for consumers by having the logo printed on the product. | IT products |
| Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) | US legislation requiring covered entities to report cyber incidents for intelligence sharing in critical infrastructure industries. | OT organizations |
| ETSI EN 303 645 | Baseline cybersecurity requirements for Consumer Internet of Things. Includes not only requirements on security features in the product to harden them against cyberattacks, but also requirements on security vulnerability reporting and communication on security update periods. | IT products |
| NIS Regulations (UK) | UK legislation regulating network and information systems, aimed at fortifying cybersecurity in critical sectors, similar to the NIS2 Directive in the EU. | IT/OT organizations |
| ISA/IEC 62443 | Standardization of processes & procedures to create more cyber secure industrial environments. Includes architecture and product hardening guidelines. Four security levels provide guidance for different levels of protection desired. | OT organizations & products |
| PSTI | The UK Product Security and Telecommunications Infrastructure (Product Security) regime puts requirements on consumer connectable products. | IT products |
| SHIELDS UP! | Initiative by the US based Cybersecurity & Infrastructure Security Agency to promote change and investment into cyber defenses. | IT/OT organizations |
| ISO 27001 | Probably the world’s most common IT Information Security Framework – a tool for risk management, cyber-resilience, and operational excellence. | IT organizations |
| EUCC | European candidate of Common Criteria certification scheme used to assure security-enforcing products introduced by the European Cybersecurity agency, ENISA. | IT/OT products |
Table 1. Summary of the main regulations, frameworks, and standards
Compliance with these cybersecurity regulations and standards will require organizations to adapt their operations and products. These changes may include implementing new processes and procedures to meet the requirements laid out by the standards. Additionally, organizations will probably need to invest in new security products to enhance the protection of their networks and devices.
The frameworks offer practical tips on how to adhere to the regulations and standards. For example, companies can use the ISO 27001 standard for the IT side of things. This standard provides requirements for an information security management system (ISMS) and is widely recognized internationally. However, ISO 27001 does not cover OT. This is where the IEC/ISA 62443 framework comes in. It picks up right where the ISO framework stops and serves as an excellent complement. The IEC/ISA 62443 provides a methodology to do a risk assessment specifically for OT.
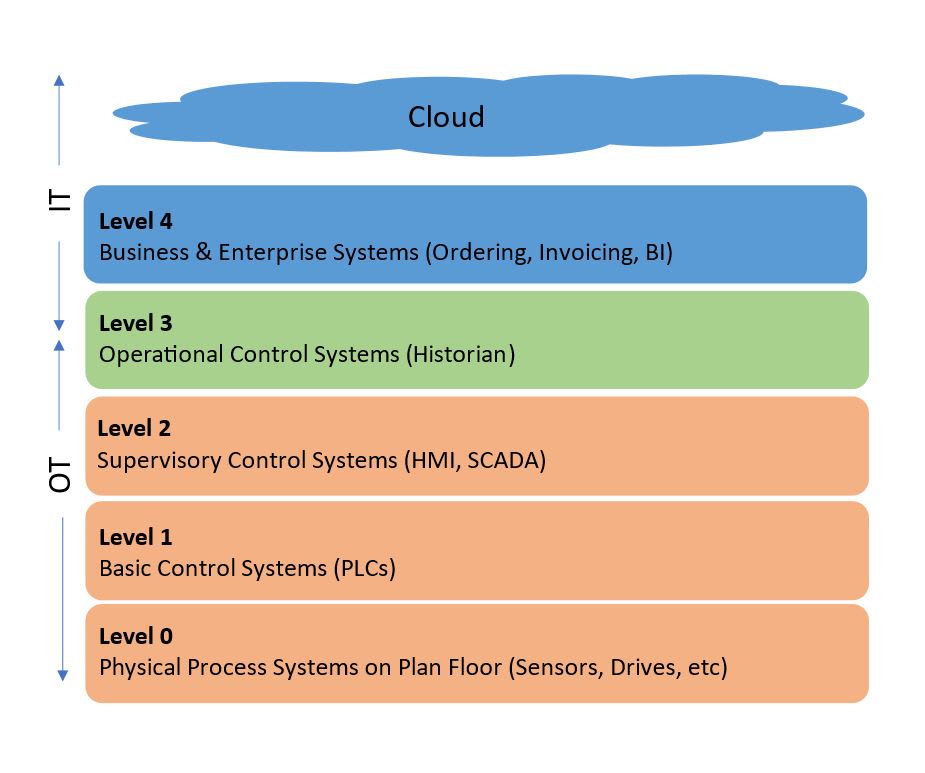
The ISO 27001 standard provides excellent guidance for IT, while the IEC/ISA 62443 covers OT.
Determining which regulation is relevant for you can be a complex task. Therefore, it’s beneficial to partner with an expert in industrial automation, industrial communication, and OT security. They can provide the expertise to interpret the guidelines and help you put measures in place to protect your assets and environments. This includes outlining requirements for resilience, detection capability, and mitigation strategies, as well as addressing specific liabilities related to reporting. Getting help from an OT focused partner is the only way to ensure focus on safety & uptime and getting the help you need to migrate your environment with those priorities in mind.
To meet regulations, asset owners need to invest in people, processes, and products. They can be overwhelmed with different offerings; many solutions exist but the buyers’ journey is complex and untransparent. Key elements of an OT security strategy should include:
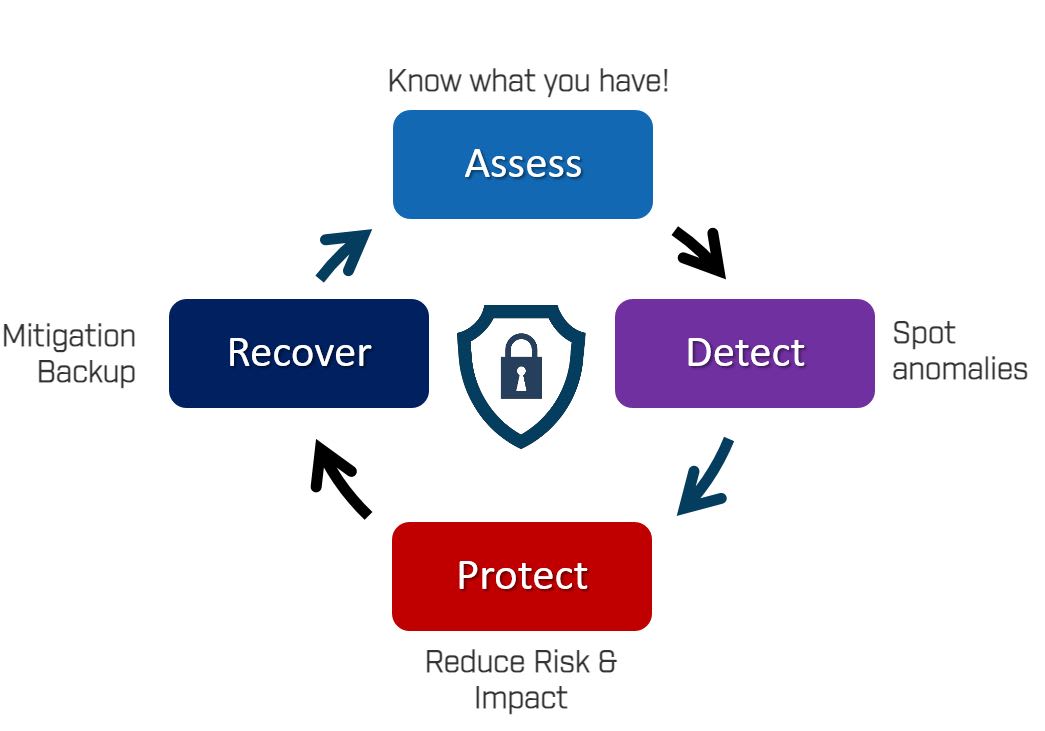
You can’t protect what you don’t know you have. What you have is also a complex question because it’s about the brand, model version, firmware, patch level – everything plays a role in understanding if the product is vulnerable or not. Understanding the asset's location within the architecture is also important, as different parts of the architecture will have varying levels of protection. While manual collection and updating of this information is possible, experience shows that it often becomes unmanageable, even in smaller networks.
When you get a tool to help with assessing your network, you probably want it to include vulnerability management as well. This helps you receive warnings proactively when older software is increasing your risk for incidents. These are typically a non-intrusive installation, often suggestively required by regulations as well, making it an easy investment decision. There are many players offering solutions here, so choosing is tough. Pure passive solutions won’t see everything, while active discovery requires extensive knowledge of industrial protocols and practices to avoid disrupting business continuity.
Threat detection is popular not only because of regulations, but also because it's easy to implement. These solutions are just monitoring network activity, with no major architecture change required. They involve using Industrial Control Systems (ICS) security solutions for network traffic analysis and anomaly detection, integrating OT monitoring with IT operations, and conducting regular device integrity checks and behavioral analysis. Centralized logging and SIEM systems help correlate events, while OT-specific threat intelligence and industry collaboration keep security measures up to date. Implementing these systems helps visualize what’s happening on your operational network and ensures compliance with reporting requirements like the one mentioned in the NIS2 directive.
However, even with asset inventory and threat detection/monitoring in place, it is important to understand that while these systems and processes provide good intelligence, they do not protect you!
Industrial firewalls are specialized security devices designed to protect OT networks and ICS from cyber threats. Unlike traditional IT firewalls, industrial firewalls are tailored to handle the unique protocols and traffic patterns found in industrial environments. They provide robust segmentation by isolating critical systems, thereby preventing unauthorized access and containing potential threats within specific network segments. These firewalls can enforce strict access controls, monitor communication flows, and detect anomalies in real-time. By integrating seamlessly with existing industrial networks, they enhance security without disrupting operational processes, ensuring both safety and reliability of critical infrastructure.
Mitigation and backup tools are crucial for safeguarding OT environments. These include data backup solutions for regular backups of PLC configurations, scheduled backups, configuration backup tools for quick restoration of device settings, comprehensive disaster recovery plans, and redundancy mechanisms to ensure operational continuity. Mitigation strategies enable rapid action by, for instance, closing off services, quarantining files or shutting down critical products to reduce further impact to operations. Together, these tools and processes help maintain the integrity, availability, and reliability of critical industrial processes and infrastructure.
Assume breach – it will happen to you! Develop a strategy that protects your assets, minimizes risk, and maximizes uptime!
Navigating cybersecurity regulations and standards is a complex but essential task for organizations operating in industrial environments. By partnering with HMS Networks and leveraging their expertise and security products, organizations can ensure compliance, enhance protection, and maximize uptime in today's ever-changing cybersecurity landscape.
Have any questions or need assistance? Reach out to us here
Thomas Vasen is Business Development Manager Network Security at Anybus, a division of HMS Networks. With over 25 years of experience in operations and security within telecom, military and critical infrastructures, Thomas now focuses specifically on helping companies managing risks and securing the uptime in their operational technology (OT) environments.


Network security products - Discover the variety of industrial network security appliances that will elevate network protection.