With reports of cyberattacks on the industrial sector becoming all too familiar, Thomas Vasen, Anybus Business Development Manager Network Security at HMS Networks, outlines five strategies companies can adopt to fortify their defenses and avoid becoming the latest victim.

Cybersecurity is rapidly becoming a significant concern in industrial automation. The World Economic Forum highlighted in 2023 that manufacturing is the sector most targeted to cyberattacks. Furthermore, Orange Cyberdefense reports that the manufacturing sector had Common Vulnerability Scoring System (CVSS) severity scores 33% higher than the global average. The increasing number of attacks on Industrial Control Systems (ICS) is particularly worrying. Gartner predicts a bleak future: by 2025, cyberattacks are expected to harm or endanger humans.
The time for action is now. Here are five strategies companies can adopt to effectively mitigate the risk of cyberattacks.
The first step is to adopt the correct mindset. In the 1990s, Netheads vs Bellheads debated the future of telecommunications. While Bellheads advocated for traditional methods, Netheads argued that voice should be treated like any other data and transmitted over IP. Three decades later, Netheads’ vision has prevailed, with voice being transmitted over the Internet like any other type of data. Users have even come to accept deterioration in call quality due to the increase in latency and frequently dropped packets. Today every phone call feels like an intercontinental one.
However, the situation with Operational Technology (OT) is fundamentally different. Unlike Information Technology (IT), OT cannot tolerate compromised quality and increased latency, as even minor disruptions can have catastrophic consequences. Treating OT as merely another version of IT is a serious mistake, as OT operates under distinct principles and requirements. While IT prioritizes data integrity and confidentiality, OT demands deterministic data and uptime assurance. This distinction is especially critical in industries like manufacturing, where even minor disruptions can lead to significant financial losses, material wastage, and operational downtime. In IT, occasional network downtime or data loss may be manageable inconveniences. However, in OT, a similar disruption can have far more severe consequences. Imagine if an ice cream machine were to malfunction due to a network outage or data inconsistency. Not only would the production process grind to a halt, but the perishable ingredients would spoil, resulting in financial losses and wasted ice cream. And nobody wants that.

Figure 1: In OT, network downtime would lead to production processes grinding to a halt, resulting in financial losses, and wasted ingredients or materials.
So, while it’s natural for OT to adopt IT technologies (there are lots of benefits of using Industrial Ethernet over traditional fieldbus networks) it must be acknowledged that out of the box IT does not satisfy OT’s requirements. Hence, the rise of industrial communications protocols, and as such, the need for specialized OT security products and solutions.
While the Chief Information Security Officers (CISO) is under scrutiny and manages the security budget, often including that for OT, it is the operations manager who bears the responsibility of ensuring uninterrupted production in the factory. This situation creates an inherent conflict due to differing priorities. IT professionals adhere to the CIA framework, prioritizing Confidentiality first, followed by Integrity and then Availability. In contrast, operational personnel prioritize Safety, followed by Availability, Integrity, and lastly, Confidentiality – forming the (S)AIC sequence.
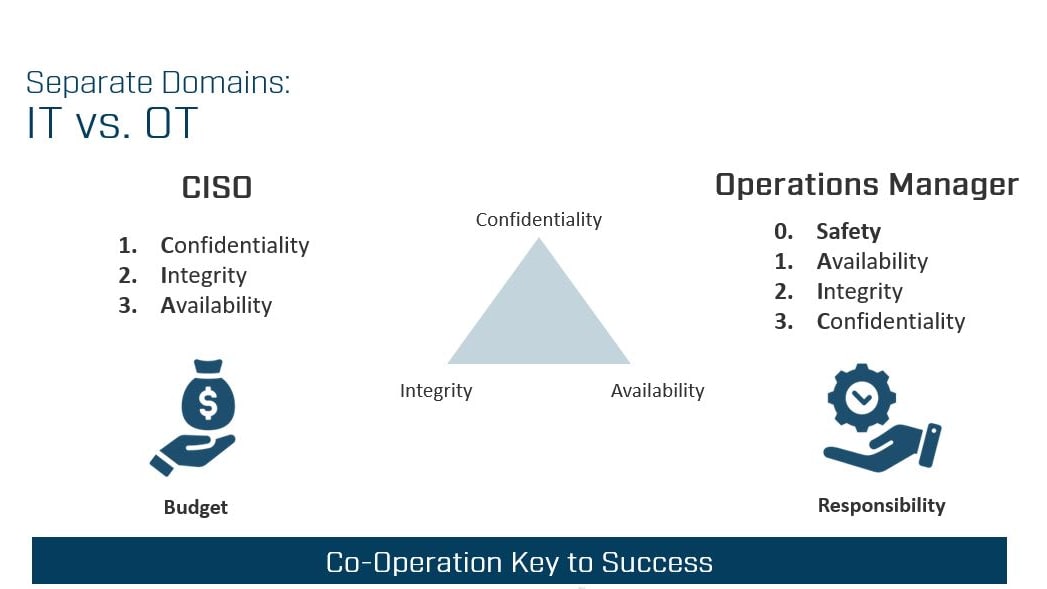
This dichotomy results in conflict and friction, yet the underlying shared objective remains clear: safeguarding business continuity. Recognizing this common goal, CISO (IT) and the Operations Manager (OT) must collaborate to navigate these challenges and harmonize their approaches to secure business continuity.
Securing OT environments requires a proactive and customized approach to the unique challenges of industrial operations. Companies must conduct a thorough identification and assessment of their assets, understanding the risks associated with each machine. Rapid detection of anomalies is important, but more crucial is the implementation of robust protective measures to safeguard these assets. Having a comprehensive recovery plan in place and implementing measures to minimize impact is also important and is commonly recommended by experts such as those from ISA/IEC 62334.
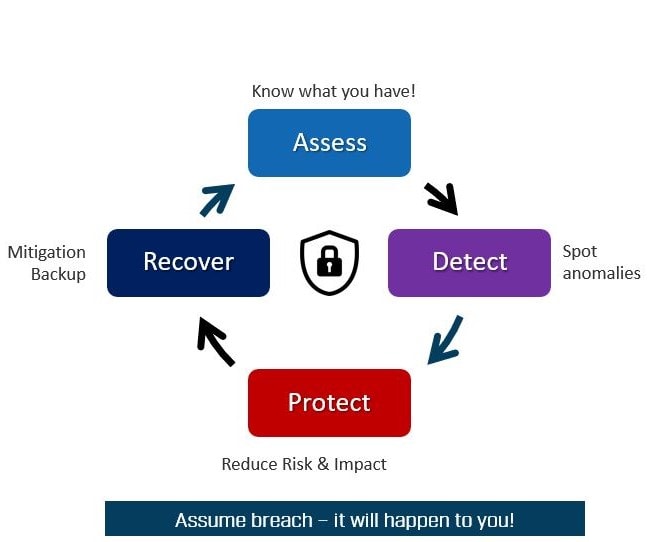
Currently, many companies focus on asset inventory and threat detection. While these are important, they are not sufficient to protect OT environments. Companies must also implement measures to protect their assets.
Network segmentation is an excellent way to secure OT environments. By dividing networks into zones and separating with conduits providing access controls, companies can bolster security and prevent unauthorized access. The benefits of network segmentation include:
Segmentation differs inherently from IT's perimeter protection approach. In IT network protection, measures are implemented to prevent outside threats from infiltrating the network, while also enabling users to freely browse the internet and utilize a wide range of cloud services. However, for OT segmentation, the focus is on exerting control in both directions to compensate for the lack in access control in OT that exists in IT. OT segmentation uses a deny-by-default approach where every flow in each direction is controlled, as threats can originate from multiple directions.
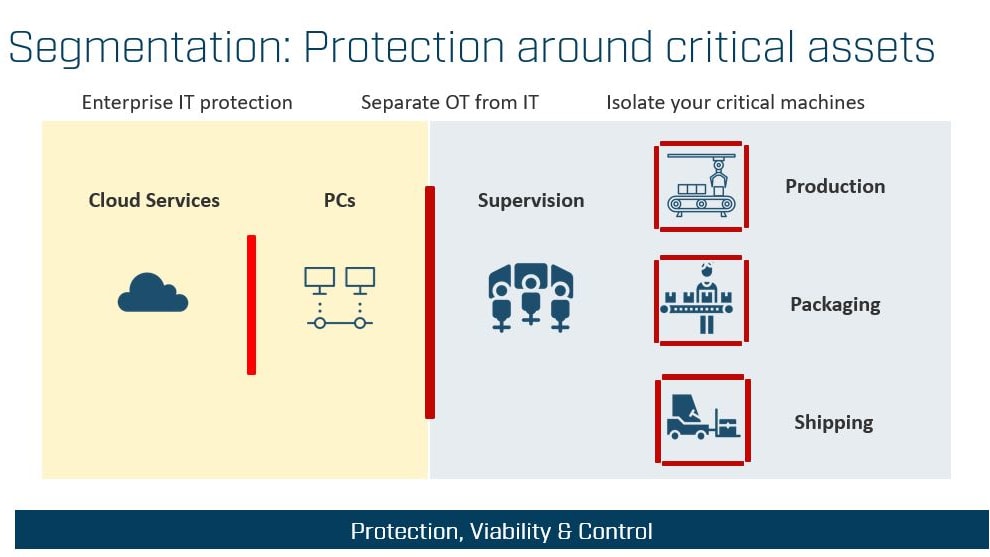
So no, OT is not just another form of IT. Implementing cybersecurity measures in industrial automation is undeniably complex and demanding work. It requires meticulous attention to detail and a deep understanding of the unique challenges presented by OT environments. Partnering with an OT expert like HMS Networks is not just a good idea; it's a smart investment. By leveraging their extensive experience and specialized knowledge, companies can save time and, more importantly, ensure that their cybersecurity strategy is effective. With HMS Networks' products and support, companies can navigate the complexities of OT cybersecurity with confidence and peace of mind.

Thomas Vasen is Business Development Manager Network Security at Anybus, a division of HMS Networks. With over 25 years of experience in operations and security within telecom, military and critical infrastructures, Thomas now focuses specifically on helping companies managing risks and securing the uptime in their operational technology (OT) environments.